CC
CRIMINALITATE CIBERNETICĂ
Seminar
VI. Elemente de investigație în criminalitatea cibernetică.
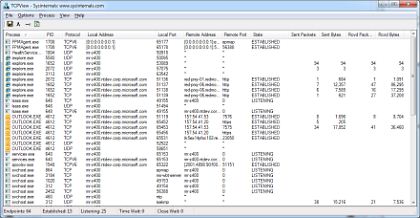
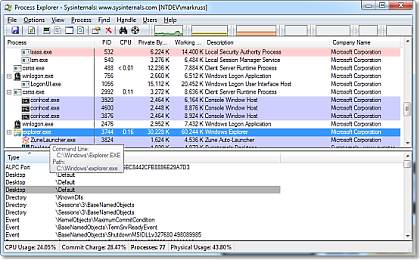
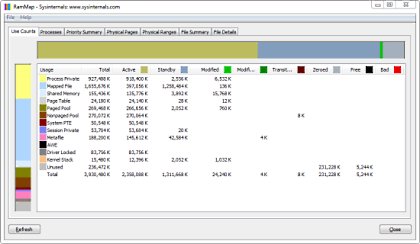
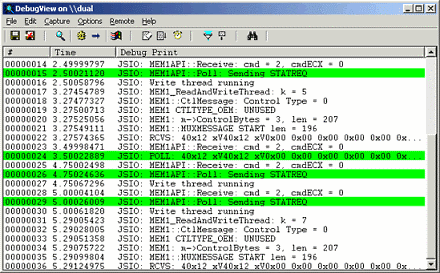
A. Windows Sysinternals
Instrumente care ajută la gestionarea, depanarea și diagnosticarea sistemelor și aplicațiilor Windows


B. Steganografia
- ascunde mesaje sau alte informații în diferite medii
Exemplu
$ steghide embed -cf picture.jpg -ef secret.txt

$ steghide extract -sf picture.jpg

Dimensiune fisiere
ls .\imagine-*
---- ------------- ------ ----
-a---- 11/12/2020 4:13 AM 56420 imagine-CuMesaj.jpg
-a---- 11/12/2020 4:08 AM 55605 imagine-Originala.jpg
Analiză Strings
.\strings.exe .\imagine-Originala.jpg > strOrg.txt
.\strings.exe .\imagine-CuMesaj.jpg > strMsg.txt
----------------------------
Strings v2.53 - Search for ANSI and Unicode strings in binary images.
Copyright (C) 1999-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
JFIF
"$"
1AQ
"aq
#BR
Sbr
%4DEVst
6Fd
"2q
#SbC$3c
4uR
d[d
]L]VIT
dkDR
/nUL
-------------------------------
Strings v2.53 - Search for ANSI and Unicode strings in binary images.
Copyright (C) 1999-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
JFIF
"$"
!1A
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
LP;
Ko x
W-L
Rw;)
-Ufc
8SD
14=[
-6\
0j!V
R3m'
l:R
CN5"
6Lc
M\b
Forensics Activities
01: Exploring the Windows File System
02: Exploring the Linux File System
03: Introduction to Partitions
04: Forensic Acquisition Using Linux Tools
05: Obtaining and Analyzing Memory
06: Linux OS Artifact Forensics
07: Windows OS Artifact Forensics
08: Windows Registry Forensics
09: Web Browser Forensics
10: Network Forensics
11: Introduction to Autopsy
12: Introduction to Digital Forensics Framework
13: Data Carving
14: Email Forensics
15: Steganography
16: Introduction to Android OS
17: Android Logical Acquisition
18: Recovering Passwords
19: Log Analysis
Exemplu de mediu de lucru
Aplicații:
Autopsy® is a digital forensics platform and graphical interface to The Sleuth Kit® and other digital forensics tools. It is used by law enforcement, military, and corporate examiners to investigate what happened on a computer. You can even use it to recover photos from your camera's memory card.
- GitHub - sleuthkit/autopsy_addon_modules: Repo to store compiled modules or links to 3rd party add-on modules.
- Eric Zimmerman's tools
- AmcacheParser
- AppCompatCacheParser
- Registry Explorer/RECmd
- ShellBags Explorer
- JumpList Explorer
- Timeline Explorer
- MFTExplorer
- WxTCmd
- Active@ KillDisk Freeware (Windows, Linux, MacOS X) for Home & Personal Use
- HxD - Freeware Hex Editor and Disk Editor | mh-nexus
- Active@ Disk Editor - Freeware Hex Viewer & Hex Editor for raw sectors/clusters (disk-editor.org)
- Link Parser - 4Discovery
- FTK Imager Version 4.5 | AccessData
- DCode™ – Timestamp Decoder - Digital Detective (digital-detective.net)
- ExifTool by Phil Harvey
- View the content of Windows Prefetch (.pf) files (nirsoft.net)
- etc.
Referinte
[3] Download Sysinternals Suite
[4] Mark Russinovich, Aaron Margosis, Troubleshooting With The Windows Sysinternals Tools, Microsoft Press, 2016
[5] Pavel Yosifovich, Alex Ionescu, Mark E. Russinovich, David A. Solomon, Windows Internals, Part 1: System architecture, processes, threads, memory management, and more [7 ed.], Microsoft Press, 2017
Resurse
Lucrările vor fi trimise spre evaluare prin Google Classroom
si numai in mod exceptional la adresa: evaluare-CC@stud.usv.ro
Proiectele, până în ultima săptămână din semestru
Referatele, până în ziua premergătoare colocviului


