CSC
CRIPTOGRAFIE ȘI SECURITATE CIBERNETICĂ
Laborator
6. Securitatea comunicațiilor web
|
Apache httpd : Basic Auth + LDAP
|
|
Configure [mod_ldap] to use LDAP directory users on httpd Basic authentication.
On this example, it uses Active Directory like following environment for it.
|
|||||||||||
| [1] |
Username and password are sent with plain text on Basic Authentication,
so Use secure connection with SSL/TLS setting, refer to here. |
||||||||||
| [2] |
Create a user on Active Directory for binding Active Directory from httpd.
On this example, it creates [ldapuser], it's OK to grant [Domain Users] rights only for it. |
||||||||||
| [3] | Install [mod_ldap]. |
|
[root@www ~]# dnf -y install mod_ldap
|
| [4] | Configure Basic authentication + LDAP. For example, set Basic Authentication to the directory [/var/www/html/auth-ldap]. |
|
[root@www ~]#
vi /etc/httpd/conf.d/authnz_ldap.conf # create new # on example below, it limits the range to search the directory only [LDAPUsers] OU # so only users under the [LDAPUsers] OU can authenticate with this setting # for [AuthLDAPBindDN] and [AuthLDAPBindPassword], specify the AD user for binding <Directory "/var/www/html/auth-ldap">
SSLRequireSSL
AuthType Basic
AuthName "LDAP Authentication"
AuthBasicProvider ldap
AuthLDAPURL "ldap://fd3s.srv.world:389/ou=LDAPUsers,dc=srv,dc=world?sAMAccountName?sub?(objectClass=*)"
AuthLDAPBindDN ldapuser@srv.world
AuthLDAPBindPassword Password
Require valid-user
</Directory>
[root@www ~]#
chgrp apache /etc/httpd/conf.d/authnz_ldap.conf [root@www ~]# chmod 640 /etc/httpd/conf.d/authnz_ldap.conf [root@www ~]# systemctl restart httpd # create a test page [root@www ~]# mkdir /var/www/html/auth-ldap [root@www ~]# vi /var/www/html/auth-ldap/index.html <html> <body> <div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;"> Test Page for LDAP Authentication </div> </body> </html> |
| [5] | If SELinux is enabled, change policy like follows. |
|
[root@www ~]# setsebool -P httpd_can_network_connect on [root@www ~]# setsebool -P httpd_can_connect_ldap on |
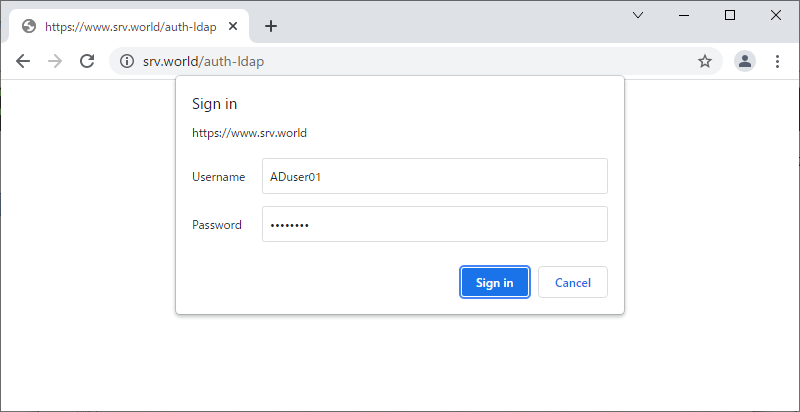
| [6] | Access to the test page from any client computer with web browser. Then authentication is required as settings, answer with any AD user. |
|
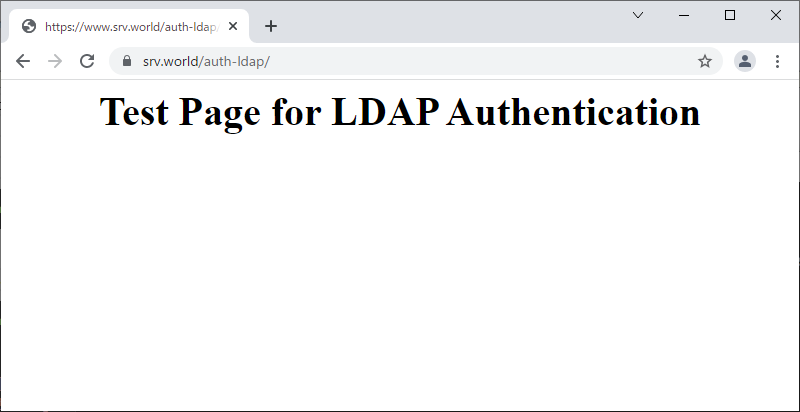
| [7] | That's OK if authentication is successfully passed and test page is displayed normally. |
|
...
